Section 3 – Implement Switch based Layer 3 services, given a network design and a set of requirements
QUESTION NO: 6
Refer to the exhibit. PCs in VLAN 2 are not able to communicate with PCs in VLAN 3. What could be the cause?
A. VTP is not configured correctly on the interfaces.
B. The command "mls rp ip" must be disabled to enable the routing.
C. The command "mls rp management-interface" is missing.
D. IP routing is not enabled.
Answer: D
Explanation:
To transport packets between VLANs, you must use a Layer 3 device. Traditionally, this has been a router’s function. The router must have a physical or logical connection to each VLAN so that it can forward packets between them. This is known as interVLAN routing.
Multilayer switches can perform both Layer 2 switching and interVLAN routing, as appropriate.
Layer 2 switching occurs between interfaces that are assigned to Layer 2 VLANs or Layer 2 trunks. Layer 3 switching can occur between any type of interface, as long as the interface can have a Layer 3 address assigned to it.
The first step in troubleshooting Inter-VLAN routing is to ensure that routing is actually enabled using the show ip route command. If no entries are seen in the routing table then IP routing needs to be enabled with the command:
Switch(config)# ip routing
QUESTION NO: 7
Refer to the exhibit. Dynamic ARP inspection (DAI) is enabled on switch SW_A only. Both Host_A and Host_B acquire their IP addresses from the DHCP server connected to switch SW_A. What would the outcome be if Host_B initiated an ARP spoof attack toward Host_A ?

A.The spoof packets will be inspected at the ingress port of switch SW_A and will be permitted.
B.The spoof packets will be inspected at the ingress port of switch SW_A and will be dropped.
C.The spoof packets will not be inspected at the ingress port of switch SW_A and will be permitted.
D.The spoof packets will not be inspected at the ingress port of switch SW_A and will be dropped.
Answer: C
Explanation:
When configuring DAI, follow these guidelines and restrictions:
DAI is an ingress security feature; it does not perform any egress checking.
DAI is not effective for hosts connected to routers that do not support DAI or that do not have this feature enabled. Because man-in-the-middle attacks are limited to a single Layer 2 broadcast domain, separate the domain with DAI checks from the one with no checking. This action secures the ARP caches of hosts in the domain enabled for DAI.
DAI depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses.
When DHCP snooping is disabled or in non-DHCP environments, use ARP ACLs to permit or to deny packets.
DAI is supported on access ports, trunk ports, EtherChannel ports, and private VLAN ports.
In our example, since Company2 does not have DAI enabled (bullet point 2 above) packets will not be inspected and they will be permitted.
QUESTION NO: 8
Inter-VLAN routing has been implemented in the Pass4sure network. In VLAN routing, what are some of the disadvantages of designing a router-on-stick configuration? (Select three)
A. InterVLAN routing cannot be filtered by the router.
B. The router becomes a single point of failure for the network.
C. Routers will not route STP BPDUs.
D. There is a possibility of inadequate bandwidth for each VLAN.
E. Additional overhead on the router can occur.
F. NetFlow Switching is required for InterVLAN accounting.
Answer: BDE
Explanation:
A router connected to a switch via a single trunk link is better known as router-on-stick or even a one armed router. Since there’s only one router, if that router were to go down there’d be no backup. Since there’s only one router, that router would have to handle all the bandwidth of every
VLAN so there’s a chance it could be overloaded, as with the overhead problems of being responsible for too much.
Because traffic routed between the VLANs traverse a single physical port, there is the potential to not provide for enough bandwidth for a VLAN at any given time.
Inter-VLAN routing also does indeed require additional configuration, management, and overhead.
QUESTION NO: 9
Refer to the exhibit. Both host stations are part of the same subnet but are in different VLANs. On the basis of the information presented in the exhibit, which statement is true about an attempt to ping from host to host?
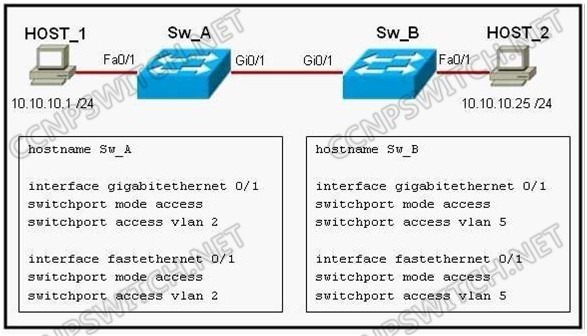
A. A trunk port will need to be configured on the link between Sw_A and Sw_B for the ping command to be successful.
B. The two different hosts will need to be in the same VLAN in order for the ping command to be successful.
C. A Layer 3 device is needed for the ping command to be successful.
D. The ping command will be successful without any further configuration changes.
Answer: D
Explanation:
Normally, to transport packets between VLANs, you must use a Layer 3 device. However, in this case the "switchport mode access" command has been used for these ports so the VLAN information will be sent along untagged. Devices that are in different VLANs can ping each other as long as they are in the same subnet when the VLAN information is untagged.
QUESTION NO: 10
Refer to the exhibit. What will happen to traffic within VLAN 14 with a source address of 172.16.10.5?

A.The traffic will be forwarded to the TCAM for further processing.
B.The traffic will be forwarded to the router processor for further processing.
C.The traffic will be dropped.
D.The traffic will be forwarded without further processing.
Answer: C
Explanation:
VLAN maps, also known as VLAN ACLs or VACLs, can filter all traffic traversing a switch. VLAN maps can be configured on the switch to filter all packets that are routed into or out of a VLAN, or are bridged within a VLAN. VLAN maps are used strictly for security packet filtering. Unlike router
ACLs, VLAN maps are not defined by direction (input or output).
To create a VLAN map and apply it to one or more VLANs, perform these steps: Create the standard or extended IP ACLs or named MAC extended ACLs to be applied to the VLAN. This access-list will select the traffic that will be either forwarded or dropped by the access-map. Only traffic matching the ‘permit’ condition in an access-list will be passed to the access-map for further processing. Enter the vlan access-map access-map-name [sequence] global configuration command to create a VLAN ACL map entry. Each access-map can have multiple entries. The order of these entries is determined by the sequence. If no sequence number is entered, accessmap entries are added with sequence numbers in increments of 10. In access map configuration mode, optionally enter an action forward or action drop. The default is to forward traffic. Also enter the match command to specify an IP packet or a non-IP packet (with only a known MAC address), and to match the packet against one or more ACLs (standard or extended). Use the vlan filter access-map-name vlan-list vlan-list global configuration command to apply a VLAN map to one or more VLANs. A single access-map can be used on multiple VLANs.