Section 1 – Implement VLAN based solution, given a network design and a set of requirements
QUESTION NO: 51
Refer to the exhibit. Switch P1S1 is not applying VLAN updates from switch P2S1. What are three reasons why this is not occurring? (Choose three.)
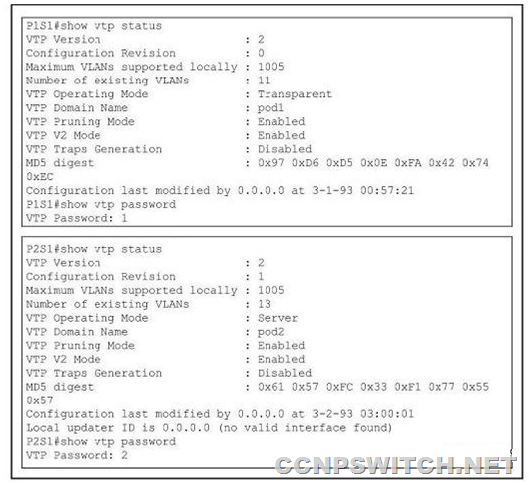
A. Switch P2S1 is in server mode.
B. Switch P1S1 is in transparent mode.
C. The MD5 digests do not match.
D. The passwords do not match.
E. The VTP domains are different.
F. VTP trap generation is disabled on both switches.
Answer: B,D,E
Explanation:
Determine the VTP mode of operation of the switch and include the mode when setting the VTP domain name information on the switch. If you leave the switch in server mode, be sure to verify that the configuration revision number is set to 0 before adding the switch to the VTP domain. It is generally recommended that you have several servers in the domain, with all other switches set to client mode for purposes of controlling VTP information.
It is also highly recommended that you use secure mode in your VTP domain. Assigning a password to the domain will accomplish this. This will prevent unauthorized switches from participating in the VTP domain. From the privileged mode or VLAN configuration mode, use the vtp password password command.
QUESTION NO: 52
The VLANs in switch R1 are being modified. Which of the following are updated in R1 every time a
VLAN is modified? (Select all that apply)
A. Configuration revision number
B. Configuration revision flag field
C. Configuration revision reset switch
D. Configuration revision database
E. None of the other alternatives apply.
Answer: A,D
Explanation:
For accountability reasons, every time a VLAN is modified the revision number changes, as does the information in the configuration revision database (as that is where the VLAN information is stored).
Incorrect Answers:
B: The configuration revision flag field, and the configuration revision reset switch don’t exist in this context.
C: The configuration revision flag field, and the configuration revision reset switch don’t exist in this context.
QUESTION NO: 53
You need to configure a new Company switch for trunking. Which switch command enables a trunking protocol that appends a four byte CRC to the packet?
A. CompanySwitch(config-if)#switchport trunk encapsulation dot1q
B. CompanySwitch(config-if)#switchport trunk encapsulation itef
C. CompanySwitch(config-if)#switchport trunk encapsulation fddi
D. CompanySwitch(config-if)#switchport trunk encapsulation isl
E. None of the other alternatives apply
Answer: D
Explanation:
The Inter-Switch Link (ISL) protocol is a Cisco proprietary method for preserving the source VLAN identification of frames passing over a trunk link. ISL performs frame identification in Layer 2 by encapsulating each frame between a header and trailer. Any Cisco switch or router device configured for ISL can process and understand the ISL VLAN information. ISL is primarily used for Ethernet media, although Cisco has included provisions to carry Token Ring, FDDI, and ATM frames over Ethernet ISL. (A Frame-Type field in the ISL header indicates the source frame type.)
When a frame is destined out a trunk link to another switch or router, ISL adds a 26-byte header and a 4-byte trailer to the frame. The source VLAN is identified with a 10-bit VLAN ID field in the header. The trailer contains a cyclic redundancy check (CRC) value to ensure the data integrity of the new encapsulated frame. Figure 6-3 shows how Ethernet frames are encapsulated and forwarded out a trunk link. Because tagging information is added at the beginning and end of each frame, ISL is sometimes referred to as double tagging.
QUESTION NO: 54
Under what circumstances should an administrator prefer local VLANs over end-to-end VLANs?
A. Eighty percent of traffic on the network is destined for Internet sites.
B. There are common sets of traffic filtering requirements for workgroups located in multiple buildings.
C. Eighty percent of a workgroup’s traffic is to the workgroup’s own local server.
D. Users are grouped into VLANs independent of physical location.
E. None of the other alternatives apply
Answer: A
Explanation:
This geographic location can be as large as an entire building or as small as a single switch inside a wiring closet. In a geographic VLAN structure, it is typical to find 80 percent of the traffic remote to the user (server farms and so on) and 20 percent of the traffic local to the user (local server, printers, and so on).
QUESTION NO: 55
While logged into a Company switch you issue the following command:
CompanySwitch(config-mst)# instance 10 vlan 11-12
What does this command accomplish?
A. It enables a PVST+ instance of 10 for vlan 11 and vlan 12
B. It enables vlan 11 and vlan 12 to be part of the MST region 10
C. It maps vlan 11 and vlan 12 to the MST instance of 10.
D. It creates an Internal Spanning Tree (IST) instance of 10 for vlan 11 and vlan 12
E. It create a Common Spanning Tree (CST) instance of 10 for vlan 11 and vlan 12
F. It starts two instances of MST, one instance for vlan 11 and another instance for vlan 12.
Answer: C
Explanation:
MST extends the IEEE 802.1w rapid spanning tree (RST) algorithm to multiple spanning trees.
This extension provides both rapid convergence and load balancing in a VLAN environment. MST converges faster than Per VLAN Spanning Tree Plus (PVST+) and is backward compatible with 802.1D STP, 802.1w (Rapid Spanning Tree Protocol [ RSTP]), and the Cisco PVST+ architecture.
MST allows you to build multiple spanning trees over trunks. You can group and associate VLANs to spanning tree instances. Each instance can have a topology independent of other spanning tree instances. This architecture provides multiple forwarding paths for data traffic and enables load balancing. Network fault tolerance is improved because a failure in one instance (forwarding path) does not affect other instances. Map the VLANs to an MST instance.
If you do not specify the vlan keyword, you can use the no keyword to unmap all the VLANs that were mapped to an MST instance.
If you specify the vlan keyword, you can use the no keyword to unmap a specified VLAN from an MST instance.
Switch( config-mst)# instance instance_number vlan vlan_range